Felipe Gacharna
- ITA Tech Instructor -
For the October 22nd ITA session, students had the option to join a choice session that explored Aviary. Aviary is a free online set of tools that allow for image editing and creation as well as music editing and creation. In particular, students got to explore the Phoenix photo editor, similar to Adobe Photoshop, the Raven vector editor, similar to Adobe Illustrator, the Myna music creator, similar to Sony ACID, and the Peacock effects editor, which is unlike most programs the students have experienced before in ITA.
All the Aviary software runs in a browser and is free for anyone to use! We used the specialized education version to great success, which allowed us to oversee much of what the students were able to accomplish in this session.
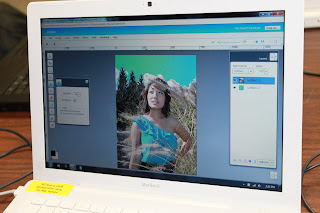
This student was very proud of the work she could do to her photo in a web browser software:
Phoenix (like Photoshop)
Phoenix has many of the same features that students have already learned in Photoshop, including layers, blending modes, filters, and the clone stamp tool, to name a few. In Phoenix, students got to play around with a base image of a hot air balloon that I provided.
Using the hot air balloon image, students were able to duplicate some of the functionality they are familiar with in Photoshop and then take it to another level with the Peacock effects editor.
Peacock (a unique photo editing tool)
You can "push" a layer from Phoenix directly to Peacock, edit the layer in Peacock, and then send it back to Phoenix. Here are some pictures of the edited hot air balloon image as well as a screen shot of the Peacock editor, showing the unique user interface.
These edited balloon images showcase some of what you can do with Phoenix and Peacock.
This screenshot of Peacock shows the "node-based user interface" that the tool uses. It's a rather unique user interface (UI) where the user is provided with "nodes" or blocks which they can manipulate. Nodes can be connected through the little "notches" on the top and on the bottom of each. These "notches" are inputs and outputs. Manipulating the inputs and outputs to each node allows for heavy manipulation of images, and since each node has its own properties that can also be manipulated, the user has a lot of power in creating a desired effect.
Here's another screenshot of Peacock showing the nodes more clearly and some manipulation done to a gradient.
Myna (sort of like Sony ACID or a drum machine)
The Myna music creator allowed students to mix sounds from a large library to create beats. Myna provides a simple interface, with several layers of different sounds and each sound having a track, with beats being on or off for a given beat. Volume can be tuned for each sound as well as for each particular beat, so students have a good amount of power in mixing their beats. Here is a screenshot of one of the beats created by a student as well as an over-the-shoulder picture of one of the students working on his Myna project.
Listen to some beats the students made:
Aviary also provides a Hall of Fame where anyone can look through submissions, as ranked by users. Most of the time, the projects actually allow you to open up the program used to create it so that users can view how the project was created. Students had an opportunity to look through the Hall of Fame to see what could be done with the tools they were using and to help them gather ideas of how they could achieve some effects in their final artifacts by looking through the projects that allowed you to see how they were created.
Wednesday, October 26, 2011
Introducing: After Effects
April Arevalo
- ITA Tech Instructor -
After Effects is a complex program that has endless possibilities of what can be created. I tend to focus a lot on text, not just what the text means but also the aesthetic feel of the text. This session I wanted the students to become familiar with the navigation and some of the functions of After Effects. The plan for this session was to give the students a basic structure of how to do a space warping text. Once the structure was complete, the students had the freedom to enhance their animation with a variety of options.
Although I felt the structure was confusing at times the students had no trouble in asking for clarification and getting back on track. Because of the complexity of this software, I had to be pretty strict about exact values for many parts of the project. However, the students were clever and had their own interpretations. They successfully came up with different text paths, styles, and compositions. This picture is a sample of a movie title as it enters the time echo effect that causes it to look like it is warping.
This picture is a sample of a movie title as it enters the time echo effect that causes it to look like it is warping.
Once the structured part of the lesson was complete and the students were introduced to backgrounds with masks and the particle world the creativity really began to flow. Approaching these two elements in more of a broad sense while still highlighting major components really played to a key aspect when using After Effects. Creating effects that are visually engaging in this program calls for experimenting or simply just playing around with the effects. The difficult part is that it requires a lot of computer processing power, so it can be a little slow going to experiment and see the results right away.
As the students dove into adding backgrounds and different particle elements it became clear that the structured part was needed and that this freedom would add another level of complexity to what the students had already made. This student made something simple look very cool and colorful.
Overall the students engagement, curiosity, patience, and creativity really made this session more than I had ever anticipated. Hopefully since this was the first session ever to use the program After Effects when other sessions are offered the students will be excited to learn and create what ever the focus of that session happens to be.
- ITA Tech Instructor -
After Effects is a complex program that has endless possibilities of what can be created. I tend to focus a lot on text, not just what the text means but also the aesthetic feel of the text. This session I wanted the students to become familiar with the navigation and some of the functions of After Effects. The plan for this session was to give the students a basic structure of how to do a space warping text. Once the structure was complete, the students had the freedom to enhance their animation with a variety of options.
Although I felt the structure was confusing at times the students had no trouble in asking for clarification and getting back on track. Because of the complexity of this software, I had to be pretty strict about exact values for many parts of the project. However, the students were clever and had their own interpretations. They successfully came up with different text paths, styles, and compositions.
 This picture is a sample of a movie title as it enters the time echo effect that causes it to look like it is warping.
This picture is a sample of a movie title as it enters the time echo effect that causes it to look like it is warping.Once the structured part of the lesson was complete and the students were introduced to backgrounds with masks and the particle world the creativity really began to flow. Approaching these two elements in more of a broad sense while still highlighting major components really played to a key aspect when using After Effects. Creating effects that are visually engaging in this program calls for experimenting or simply just playing around with the effects. The difficult part is that it requires a lot of computer processing power, so it can be a little slow going to experiment and see the results right away.
As the students dove into adding backgrounds and different particle elements it became clear that the structured part was needed and that this freedom would add another level of complexity to what the students had already made. This student made something simple look very cool and colorful.
Overall the students engagement, curiosity, patience, and creativity really made this session more than I had ever anticipated. Hopefully since this was the first session ever to use the program After Effects when other sessions are offered the students will be excited to learn and create what ever the focus of that session happens to be.
Labels:
After effects,
Custom Workshop,
ITA Session,
Movie,
particle world,
space,
Technology Labs,
text,
Visual Arts
Annual ITA Halloween Costume Contest delivers more treats than tricks
Alison Wilson
This student sported the unofficial uniform of the US Women's soccer team.






Our runner-up is a TIE between Dipsy and Raggedy Ann. Each of them will receive a $20 Best Buy gift card!

- ITA ACT and College Prep Instructor -
Each year, ITA encourages students to look deep within themselves to come up with the BEST Halloween costumes possible. While few students participated this year, the costumes did not disappoint. Not only did these students have the opportunity to go trick-or-treating in each of their classes, but ITA staff was on the lookout for the most creative, fun, inspiring, or well-executed costumes.
Without further adieu, I present to you the Halloween Costume Contest participants of 2011!
This student sported the unofficial uniform of the US Women's soccer team.


The classic masquerade mask for a sophisticated costume. Also, she loves trees...

Here is a very convincing crusader, complete with sword and chainmail!

I’m not even sure who this ninja was; this costume was just that good!

Wow! Nice interpretation of Raggedy Ann, red Converse and all! You rock!
Arrrrrr, mateys! This here be another ITA student as a pirate!
We even had a mime costume. And, some nice miming talent along with it!

With so many AWESOME costumes, it was difficult for staff to choose the winners. In the end, it all came down to just a few votes…
Our runner-up is a TIE between Dipsy and Raggedy Ann. Each of them will receive a $20 Best Buy gift card!

This year’s costume contest winner is the robot from LMFAO’s “Party Rock Anthem” music video. He will receive an iPod shuffle and a $15 iTunes gift card!

A huge thanks to Mary, Sarah, Brianna, Brenna, Ian, Ninoska, Adrian, Josh K., and Islam ! You will each receive a raffle ticket for the End-of-Semester prize raffle!!
Photos by: A.J. Daughtry Krill
Photos by: A.J. Daughtry Krill
Labels:
Acting,
Art,
Community,
Competition,
Contest,
Costume,
Creativity,
ITA Events,
ITA Session
Sunday, October 23, 2011
Computer Security
For the first choice session of the year, a workshop focused on computer security titled Hack This! was offered. The session began by looking at a comparison of families of operating systems. A diagram of UNIX and Unix-like systems can be found here.
Here are some of the major topics we covered in class to give students a better understanding of how computer security works, and how to stay safe in a deeper level than we usually have time for...
Windows Password Security
Losing a Windows password happens quite often, especially when the user is no longer a part of the organization, or has simply forgotten the password for the only administrator account on a rarely-used system. There are several options, which you can research on your own. Our students got to try a few. It was helpful for them to learn just why it's so important to have not only a good password, but other layers of protection as well.
Mac Password Security
Mac has the reputation of being pretty secure and safe, but their efforts to be as user-friendly as possible and building everything on a UNIX platform platform have left some vulnerabilities.
In order to gain access to a Mac with a lost administrator password, the best way is to use the Mac OSX Install disc that came with the computer. There are other ways to secure your Mac and help you to remember your password that the students had a chance to discuss as well, including encrypting actual files as well as the OS.
Cracking file-level passwords
While we discovered that user passwords for operating systems are rather unsecure, password encryption for files can be very difficult to crack. We looked at the differences between methods of password cracking, such as Hash decryption, Dictionary set, and Brute force. More information on these methods can be found at: http://en.wikipedia.org/wiki/Password_cracking
Students had a much better understanding of how threats to security occur, and they learned the importance of being very careful when storing information, especially sensitive information.
Live CDs
We booted our computers using Puppy Linux and Knoppix, though we discussed the use of even more alternatives, such as Ubuntu derivaties that can run live, as well as BackTrack, DEFT, and MilaX. A more complete list of LiveCDs can be found here. These live CDs are ways to boot a computer with a non-functioning operating system and access the hard drive. They are an important part of any IT toolkit for retrieving data and also running a full virus scan that can check for rootkits while the primary operating system is offline. With these tools, students can learn a really safe way to recover important work they thought they had lost to a virus or other OS corruption!
Internet Security
We took a tour of www.whatsmyip.org to explore some of the information that is passed on to a website about every visitor and ways that one can protect a computer against malicious attacks by testing what vulnerabilities exist. Using this website, we were able to discuss how to make passwords more secure, geolocation, proxy servers, MD5 checksum. This also led to a discussion to ports, firewalls and creating a DMZ using a dual-firewall setup.
In the End
Of course, our conversation went to all sorts of places, and our students seemed to learn and share a whole lot about the way computers work, the way to work around that, and most of all the importance of having a better understanding of this still somewhat new frontier of online life.
Here are some of the major topics we covered in class to give students a better understanding of how computer security works, and how to stay safe in a deeper level than we usually have time for...
Windows Password Security
Losing a Windows password happens quite often, especially when the user is no longer a part of the organization, or has simply forgotten the password for the only administrator account on a rarely-used system. There are several options, which you can research on your own. Our students got to try a few. It was helpful for them to learn just why it's so important to have not only a good password, but other layers of protection as well.
Mac Password Security
Mac has the reputation of being pretty secure and safe, but their efforts to be as user-friendly as possible and building everything on a UNIX platform platform have left some vulnerabilities.
In order to gain access to a Mac with a lost administrator password, the best way is to use the Mac OSX Install disc that came with the computer. There are other ways to secure your Mac and help you to remember your password that the students had a chance to discuss as well, including encrypting actual files as well as the OS.
Cracking file-level passwords
While we discovered that user passwords for operating systems are rather unsecure, password encryption for files can be very difficult to crack. We looked at the differences between methods of password cracking, such as Hash decryption, Dictionary set, and Brute force. More information on these methods can be found at: http://en.wikipedia.org/wiki/Password_cracking
Students had a much better understanding of how threats to security occur, and they learned the importance of being very careful when storing information, especially sensitive information.
Live CDs
We booted our computers using Puppy Linux and Knoppix, though we discussed the use of even more alternatives, such as Ubuntu derivaties that can run live, as well as BackTrack, DEFT, and MilaX. A more complete list of LiveCDs can be found here. These live CDs are ways to boot a computer with a non-functioning operating system and access the hard drive. They are an important part of any IT toolkit for retrieving data and also running a full virus scan that can check for rootkits while the primary operating system is offline. With these tools, students can learn a really safe way to recover important work they thought they had lost to a virus or other OS corruption!
Internet Security
We took a tour of www.whatsmyip.org to explore some of the information that is passed on to a website about every visitor and ways that one can protect a computer against malicious attacks by testing what vulnerabilities exist. Using this website, we were able to discuss how to make passwords more secure, geolocation, proxy servers, MD5 checksum. This also led to a discussion to ports, firewalls and creating a DMZ using a dual-firewall setup.
In the End
Of course, our conversation went to all sorts of places, and our students seemed to learn and share a whole lot about the way computers work, the way to work around that, and most of all the importance of having a better understanding of this still somewhat new frontier of online life.
Labels:
Choice Session,
Drivers,
Hardware,
History,
linux,
mac,
Open Source,
Operating Systems,
password,
Programming,
Scanning,
security,
Technology Labs,
windows
Subscribe to:
Posts (Atom)